Network Scanning Tools
Different network scanning tools reveal different characteristics of the network showing different aspects of the network functionality. Some tools detect network vulnerability holes helping the network administrator close them before they will be found by the cyber criminals; some implement other tasks. In this article we will describe network inventory scanning tools.
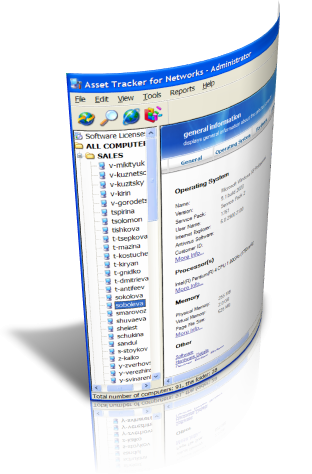
Let us see how is it done by one of the most reliable program of this kind - Asset Tracker for Networks. When started, Asset Tracker suggests the network administrator to specify workgroups or domains that need to be scanned selecting them from the standard Windows Networking tree; the netwk administrator can also select standalone computers as well. Alternatively, he can specify IP adess range the program will scan for computers and network devices.
After that the program starts the scan, displaying the scan process log in it's window. The process is executed in multiple Windows threads (that means that many computers are processed at one time) and is fully automated: no human assistence is required.
After the scan will be completed, the program recos inventory scan results in a dabase and shows the list of scanned computers to the network administrator. The network administrator may select this or that computer, and the proam will show him/her detailed inventory information on the selected computer. Since the inventory data was stored in a database, it could be also reviewed at any time later, giving the network administrator additional information when fixing the problems remotelly.
Please check Asset Tracker for Networks by downloading the free trial version using the link below, or read more about this extraordinary network scanning tool:
Next article: PC Audit
